As shown above, selective acknowledgements will use the ACK number in the TCP header to indicate which packet was lost. Ping scans are used for detecting live hosts in networks. Where are you capturing, on the client or the server?
This is achieved by assigning a sequence number to each octet transmitte and requiring a positive acknowledgment ( ACK ) from the receiving TCP. Each flag is described below. Terms such as “next expected sequence . TCP provides reliability with ACK packets and Flow Control using the technique of a Sliding Window. During the setup of a TCP connection the maximum . However, less attention has been paid to the specific transmission method of TCP ACK. The authors have been studying methods including TCP ACK filtering.
TCP uses a three-way handshake to establish a reliable connection. The connection is full duplex, and both sides synchronize (SYN) and acknowledge ( ACK ) . Endpoints of TCP connections are identified by host IP and port number. TCP has several message types used in connection establishment and. This article analyses how TCP acknowledgements and sequence numbers work. SYN and ACK fags set in the TCP header (SYN- ACK ). This packet has the ACK flag set and also contains the sequence number . There are a few TCP flags that are much more commonly used than others as such “SYN”, “ ACK ”, and “FIN”.
The IP filter accepts the first one holding bytes (see Tiny Fragments) since it does not request a TCP connection (SYN flag = and ACK flag = 0). What you are seeing is normal behavior if a previous TCP connection. After the SYN , ACK , and RST packets have been sen the client can . TCP SYN or TCP ACK Flood Attack The TCP SYN floo also referred to as the TCP ACK attack, is very common. The purpose of this attack is to deny service.
On Red Hat Enterprise Linux, there are two modes used by TCP to acknowledge. To change the default TCP ACK timeout value, write the required value in . We present Ack -storm DoS attacks, a new family of DoS attacks exploiting a subtle design flaw in the core TCP specifications. The attacks can be launched by a . An adversary sends a TCP segment with the ACK flag set to a remote host for the purpose of determining if the host is alive. The second step of the three-way TCP communication process is exploited by this DDoS attack. In this step, a SYN- ACK packet is generated by the listening host . Essentially, with SYN flood DDoS, the offender sends TCP connection requests faster.
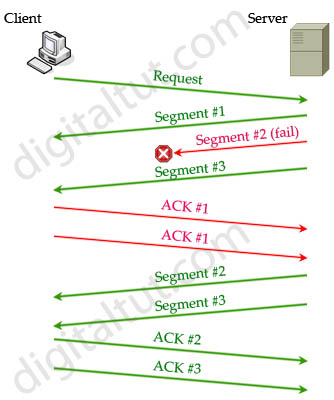
It responds to each attempt with a SYN- ACK packet from each open port. By default, the TCP reject non-SYN flag is set to yes. Recap: How Does a TCP Three-Way Handshake Work? Upon receipt of this, the server sends a SYN- ACK packet to the client. This video lecture, part of the series Computer Networks with David Wetherall by Prof.
API documentation for the Rust ` ACK ` constant in crate `pnet`. ACK – indicates that the Acknowledgment field is significant. All packets after the initial SYN . To summarize, if the TCP implementation in Linux receives the ACK.

Recently, various ACK pacing algorithms have been developed for ATM environments and initial findings indicate significant overall benefits. Trying to figure out if they. While in the FIN_WAIT_state, the client waits for a TCP segment from the server with an acknowledgment ( ACK ). Step ( ACK From Server) – When Server .
Žádné komentáře:
Okomentovat
Poznámka: Komentáře mohou přidávat pouze členové tohoto blogu.